According to Locard's Exchange Principle, every interaction leaves a trace, a concept that applies equally well in digital forensics. In this field, timeline analysis plays a vital role in identifying a user's past activities. It can reconstruct the sequence of events on a machine, revealing what occurred and the actions taken, which is invaluable for tracking an adversary's presence within a system.
So now what is Time Analysis?
Timeline Analysis is a technique used in Digital Forensics or Incident Response with the help of a tool that provides insight into activities performed on a machine. It compiles and organizes various artifacts—such as registry entries, program executions, file system changes, file downloads, browser history, and other operating system artifacts—into a time-ordered sequence. This chronological arrangement of data enables investigators to trace user activities and understand the events that transpired in the system.
Timeline Analysis helps identify adversaries' footprints, detect the use of anti-forensic tools, and uncover other activities that occurred during an incident. This technique provides you very wealth of information at the same time timeline analysis is cumbersome as results will provide you with a lot of noise (System File Artifacts, Event Logs, etc) so it is the task of the investigator to remove system noise from the timeline results.
So in this post, we are going to cover basic timeline analysis techniques using $USNJrnl Artifacts with the help of a fictional case study.
What is USNJrnl?
“The USN Journal (Update Sequence Number Journal), or Change Journal,[1] is a feature of the Windows NT file system (NTFS) which maintains a record of changes made to the volume.”
- Wikipedia
It is a high-level summary of changes to files and directories, along with codes indicating the types of changes, is recorded. This information is also used by the Windows Backup Application to identify recently modified files and determine which files need to be backed up.
USNJrnl Reason code will help the investigator analyze so one must be aware of this below-mentioned reason code to analyze the timeline activity using USNJrnl
USNJrnl Location: $Extend$UsnJrnl
Reason Code: https://learn.microsoft.com/en-us/windows/win32/api/winioctl/ns-winioctl-usn_record_v3
Case Study:
LEA have detained Hacker committed computer hacking and identity theft violations in conjunction with the theft and release of personally identifiable information (PII) of Government service members and federal employees. As alleged in the criminal complaint, also known by his hacking moniker “Jinmori,” is believed to be the leader of an internet hacking group called Elite Hunters Group.
As per intelligence arrested person was working on Malware that Targets SCADA which was programmable logic controllers (PLCs) and he used Living off the Land Wipers to wipe the traces of Malware before arrest.
Now I'm going to use one of the best and my favourite tools by Eric Zimmerman.
The tool used for the Analysis:
FTK Imager: It is used to extract the $USNJrnl from the file system
PECMD by Eric Zimmerman - prefetch parser (You can refer my previous post on prefetch for more details)
MFTECmd is also capable of parsing the $J, $Boot and $LogFile
Timeline Explorer - To Analyze the extracted Journal File.
Here is below procedure to analyze prefetch artifacts for more details on prefetch you can refer my previous article
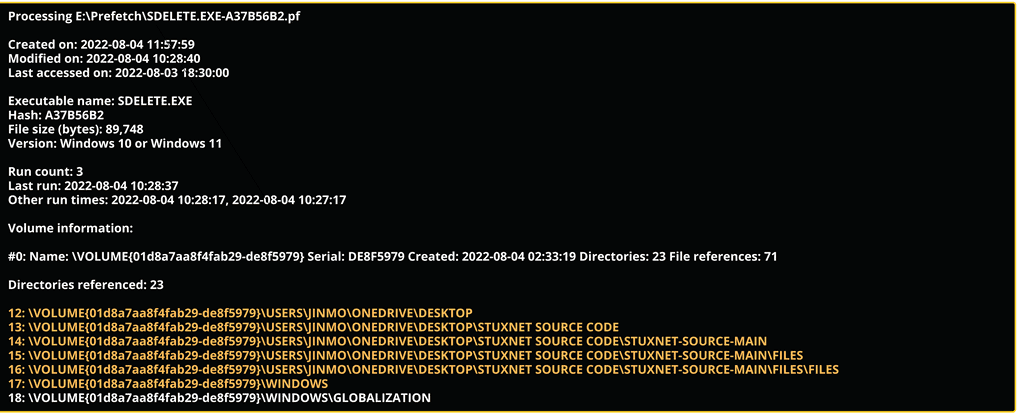
We can observe , the results fetched by the PECMD command for the SDELETE.EXE-A37B56B2.pf prefetch file concludes that SDelete has touched File's and Directory of the Stuxnet (Source Code Folder) within 10 seconds. SDelete application is Living off the Land Wipers which was used by user Jinmori to wipe Traces of Stuxnet Source Code.(i.e: SDelete has Wiped Stuxnet Source Code Folder which was saved in the Desktop)
Stuxnet, a computer worm, discovered in June 2010, that was specifically written to take over certain programmable industrial control systems and cause the equipment run by those systems to malfunction, all the while feeding false data to the systems monitors indicating the equipment to be running as intended.
- britannica.com
Now we know wiper name, we can further use timeline analysis technique using USNJrnl. We follow below process to extract USNJrnl and analyze it using MFTECmd and Timeline Explorer.
We can observe from below figure MFT Entry which is assigned for the Stuxnet Source Code Folder is subjected to the renaming mentioned in the update reasons of the USNJRNL entries with successive alphabetic character naming scheme as mentioned in official Microsoft Page. This concludes the usage of the SDelete Tool to wipe the Source Code Folder of Stuxnet.
To overwrite file names of a file that you delete, SDelete renames the file 26 times, each time replacing each character of the file's name with a successive alphabetic character. For instance, the first rename of "foo.txt" would be to "AAA.AAA".
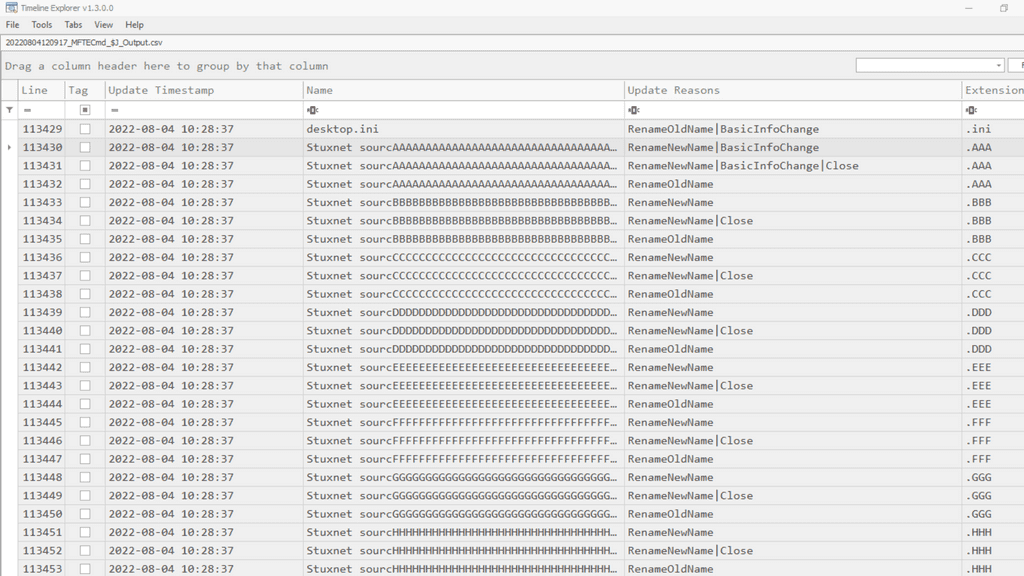
Using timeline analysis with USNJrnl, we were able to prove that the Sdelete application was used to wipe the Stuxnet source code. This is a brief example of how timeline analysis can aid forensic experts in identifying patterns of the perpetrators.
In the future, we'll explore more on timeline analysis and delve into supertimeline concepts.